Have you made a RAR file containing important information years ago and you applied a password to protect it, but now you forget the password to access it? Or you do not want to enter a password every time you want to open your RAR file? Are you wondering how can you bypass RAR/WinRAR password? Actually, there are some methods available to bypass passwords on RAR files. These methods let you bypass the password prompt and access all the contents of the archive with or without the password. Let's take a look at them.
Way 1: The 100% Working and Easiest Way to Bypass WinRAR Password
Bypass RAR Password with Third-party Software. To compromise the RAR passwords, you need to obtain the RAR Security password and set up it on your PC. PassFab for RAR is the answer to all your problems, and it works in three actions to complete the RAR password recovery. The following is the entire procedure to do the RAR password removal process with Notepad on your computer. Step 1: Locate the password protected RAR file on your computer. Right-click on the file, select Open with, click on Choose another app, and finally choose Notepad as the app.
If you're blank about the password, then the best option is using a professional WinRAR password unlocker like Passper for RAR. It is so far the easiest and most effective RAR password unlocker according to tests which focus on unlocking encrypted RAR archives created by RAR and WinRAR. It provides 4 powerful attak modes which ensure the high success rate to find the original password of the protected archive. You can use this tool on Windows 7/8/8.1/10.
Key Features of Passper for RAR:
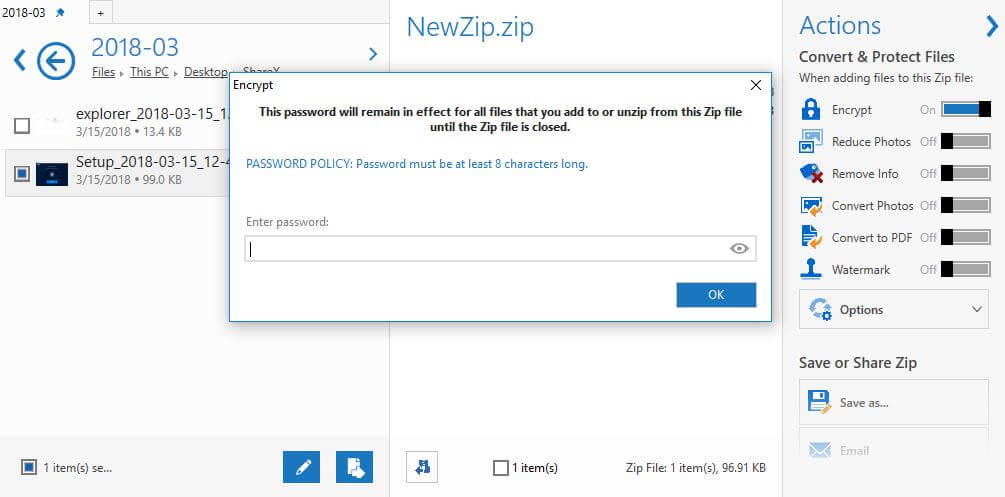
RAR is popular because of how much the file size can be compressed, as well as the powerful encryption that is built-in. With just a few clicks, you can encrypt and password-protect any RAR archive. Without the correct password, unauthorized users won't even be able to see the names of the files it contains. Password brute-force: games here: you like this video, leave a comment and subscribe!. WinRAR is an archive program designed to open archive formats such as RAR. In case of a forgotten password, you can bypass this problem by using some free software to locate the password and open the file. Download and install RAR Password Recovery (see Resources). The free version of this program has a three-character limit for passwords.
High Success Rate: Passper for RAR is well aware of the various methods of password protection, and thus applys advanced algorithm that allow you to recover forgotten RAR passwords with high success rate.
Ultrafast Recovery Speed: If you have a clue about the password, the encrypted RAR archive can be unlocked in seconds. If you know nothing about it, Passper for RAR can also quickly recover the password using CPU acceleration.
Pretty Easy to Use: The product interface is intuitive and easy to undertand, so it's easy for novice or professional users to use. And you can unlock the encrypted RAR file within 3 steps.
100% Data Security & No Data Loss: Your personal data will only be saved in your local system, therefore, your data privacy is 100% ensured. What's more, there won't be any loss or damage of your data during/after the recovery.
Save Recovery Progress: You can stop and restart the recovery process at any time, and your recovery status will be saved.
Passper is sub-brand of iMyFone, a famous tech company which is widely recognized by a lot tech site like PCWorld, techradar, thewindowsclub, tech advisor and etc. Therefore, it's totally safe to use Passper for RAR.
The following shows how to use the software on your computer to bypass RAR password.
To get started, download and install the software on your computer.
Step 1 Launch the software and click on the '+' icon to add your RAR file to the app for cracking the password. Then, choose an attack method from the list on your screen.
Note
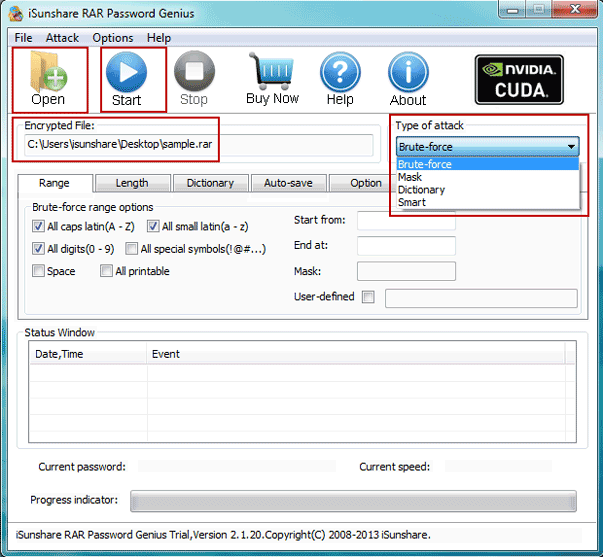
If you have clue about the password, it is recommended to choose Mask Attack and Combination Attack, you can enter some frequently used info (like you name, your birthday, you birth place) to narrow down the result and speed up the password recovery. If you know nothing about the password, you can try Dictionary Attack or simply go to Brute Force Attack to guess the original password. You can click here to know more information about how to use every attack mode.
Step 2 After choosing the attack mode, click on 'Recover' button to start RAR password recovery. As soon as the software has found the password, the password will be displayed on your screen as below.
You can also check the video guide of Passper for RAR below
Way 2: Bypass Winrar Password with CMD
You can also use command prompt to bypass WinRAR/RAR password. This is a free but very cumbersome way since you need to enter several commands. The following is how you go about doing it on your computer.
Step 1: Copy the following command line to Notepad. Then save it as bat file.
@echo off
title WinRar Password Retriever
copy 'C:Program FilesWinRARUnrar.exe'
SET PASS=0
SET TMP=TempFold
MD %TMP%
:RAR
cls
echo.
SET/P 'NAME=File Name : '
IF '%NAME%'' goto ProblemDetected
goto GPATH
:ProblemDetected
echo You can't leave this blank.
pause
goto RAR
:GPATH
SET/P 'PATH=Enter Full Path (eg: C:UsersAdminDesktop) : '
IF '%PATH%'' goto PERROR
goto NEXT
:PERROR
echo You can't leave this blank.
pause
goto RAR
:NEXT
IF EXIST '%PATH%%NAME%' GOTO SP
goto PATH
:PATH
cls
echo File couldn't be found. Make sure you include the (.RAR) extension at the end of the file's name.
pause
goto RAR
:SP
echo.
echo Breaking Password..
echo.
:START
title Processing..
SET /A PASS=%PASS%+1
UNRAR E -INUL -P%PASS% '%PATH%%NAME%' '%TMP%'
IF /I %ERRORLEVEL% EQU 0 GOTO FINISH
GOTO START
:FINISH
RD %TMP% /Q /S
Del 'Unrar.exe'
cls
title 1 Password Found
echo.
echo File = %NAME%
echo Stable Password= %PASS%
echo.
echo Press any key to exit.
pause>NUL
exit
Step 2: Double-click on the batch file to launch it. When it launches, the command prompt window will appear. You will need to enter the name and location of your password protected RAR file. Do so and continue.
Step 3: Once you have finished the above step, CMD will begin to crack the password for your RAR archive. It can take anywhere from a few seconds to a few minutes to finish cracking the password. The password will be shown on your screen when it is found.
That is all to bypass the WinRAR password using Command Prompt on your computer.
Note
This way only works for the numeric password. If your password contains letters, numbers and symbols, then you need to select other way to unlock the encrypted RAR archive.
Way 3: Bypass RAR Password Using Notepad
While Notepad is usually used for creating and editing text files, it helps bypass RAR passwords as well. There is a neat little trick that makes it possible to bypass the password prompt for your RAR files in the Notepad app. Although the recovery rate is pretty low, you can still give it a try.
Basically, the procedure involves launching your RAR file with the Notepad app. Then you change certain strings in the file to remove the password prompt. The following guide lists the entire procedure step by step for you to follow.
Step 1: Find the password protected RAR file on your computer. Right-click on the file, select Open with followed by Choose another app, and click on Notepad to open the file.
Step 2: When the file opens in Notepad, select the Edit menu at the top and click on Replace. It will let you replace a string in the file.
Step 3: Replace Ûtà with 5^3tà and 'IžC0 with IžC_0. Once the strings are replaced, save the file.
Launch your RAR file with the WinRAR app and you will notice it no longer asks you to enter a password. You have successfully removed the password from your file.
That is how you get past RAR password using Notepad on your computer.
Way 4: Bypass RAR Password Online
If you do not want to install any software on your computer to bypass the RAR password, you may use an online service that allows you to remove passwords from your RAR files on the web. But please note that, many online tools require you to upload your files to its server, this will lead to your sensitive infomation leakage. The following are the steps on how you can do the procedure without installing anything on your machine.

Step 1: Open a browser on your computer and head over to the crack zip rar online website.
Step 2: When the website has fully loaded in your browser, you need to input a valid email address. Then click 'Select file' to upload your encrypted RAR file.
Step 3: You need to tap on the 'Submit' button to start uploading your file.
Step 4: Once your file has been uploaded successfully, you will get a TaskID. Click 'Start recover' to trigger the process. If you want to check the process, you need to click the 'Click here to track it'.
Note
Even though you only need to pay for the result, I do not highly recommend this tool to you. It will take a very long time to unlock the encrypted RAR file with this online service. When tracked the recovery process of my RAR file, I found that the process started with 0.29%. Then it moved on to 0.39% and 0.49%. I still didn't get a result now.

Way 5: Official Way to Bypass WinRAR Extraction Password When You Know the Password
For some users, it is annoying to enter a password every time you want to open the RAR archive. If you know the correct password, it will be simple to bypass this password prompt. This can be accomplished with the help of WinRAR. Following is a detailed guide for you.
Step 1: Firstly, you need to download and install the WinRAR app on your computer. Then launch it.
Step 2: Open the password protected RAR archive with WinRAR app. When the file opens, click the 'Extract to' button to start extracting the RAR archive.
Step 3: Enter the correct password in the 'Enter password' dialog. Click 'OK' to continue.
Step 4: Then it will start to extract files from the RAR archive. You can then right-click on the extracted files and choose 'Add to archive' to create a completely new and unprotected RAR archive for your files.
Tip: How to Bypass RAR/WinRAR Password on Android
You may want to know how to bypass RAR/WinRAR password on Android phones. If you already know the correct password, you can download an application called ArchiDroid from Play Store to bypass the password protection. If you do not have any idea of the correct password, it may be hard to skip the RAR/WinRAR password. We have spent much time searching online, but we didn't find any application that can bypass RAR/WinRAR password on Android without knowing the correct password. Thus, the best solution for you is to choose an online service or transfer your password-protected RAR file to a Windows computer, then bypass the password with the above-mentioned methods.
What is Password Cracking?
Password cracking is the process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords. In other words, it's an art of obtaining the correct password that gives access to a system protected by an authentication method.
Password cracking employs a number of techniques to achieve its goals. The cracking process can involve either comparing stored passwords against word list or use algorithms to generate passwords that match
In this Tutorial, we will introduce you to the common password cracking techniques and the countermeasures you can implement to protect systems against such attacks.
Topics covered in this tutorial
What is password strength?
Password strength is the measure of a password's efficiency to resist password cracking attacks. The strength of a password is determined by;
- Length: the number of characters the password contains.
- Complexity: does it use a combination of letters, numbers, and symbol?
- Unpredictability: is it something that can be guessed easily by an attacker?
Let's now look at a practical example. We will use three passwords namely
1. password
2. password1
3. #password1$
Games People Play follows three women - a basketball wife trying to protect her family, a tenacious journalist trying to rebuild a tarnished career and a struggling actress looking to become a. BET has renewed 'Games People Play' starring Lauren London, Sarunas J. Jackson, Parker McKenna Posey, Karen Obilom and Jackie Long for a second season. From executive producers Tracey Edmonds, Angela Burt-Murray, Vanessa Middleton, and Kim Newton, the Games People Play TV show is a drama based on Burt-Murray's 2014 mystery novel. Games People Play (2019 TV series) From Wikipedia, the free encyclopedia Games People Play is an American drama television series, based on the novel Games Divas Play written by Angela Burt-Murray, that premiered on April 23, 2019, on BET. On November 13, 2019, the series was renewed for a.
For this example, we will use the password strength indicator of Cpanel when creating passwords. The images below show the password strengths of each of the above-listed passwords.
Note: the password used is password the strength is 1, and it's very weak.
Note: the password used is password1 the strength is 28, and it's still weak.
Winrar Password Remover
Note: The password used is #password1$ the strength is 60 and it's strong.
The higher the strength number, better the password.
Let's suppose that we have to store our above passwords using md5 encryption. We will use an online md5 hash generator to convert our passwords into md5 hashes.
The table below shows the password hashes| Password | MD5 Hash | Cpanel Strength Indicator |
|---|---|---|
| password | 5f4dcc3b5aa765d61d8327deb882cf99 | 1 |
| password1 | 7c6a180b36896a0a8c02787eeafb0e4c | 28 |
| #password1$ | 29e08fb7103c327d68327f23d8d9256c | 60 |
We will now use http://www.md5this.com/ to crack the above hashes. The images below show the password cracking results for the above passwords.
As you can see from the above results, we managed to crack the first and second passwords that had lower strength numbers. We didn't manage to crack the third password which was longer, complex and unpredictable. It had a higher strength number.
Password cracking techniques
There are a number of techniques that can be used to crack passwords. We will describe the most commonly used ones below;
- Dictionary attack– This method involves the use of a wordlist to compare against user passwords.
- Brute force attack– This method is similar to the dictionary attack. Brute force attacks use algorithms that combine alpha-numeric characters and symbols to come up with passwords for the attack. For example, a password of the value 'password' can also be tried as p@$$word using the brute force attack.
- Rainbow table attack– This method uses pre-computed hashes. Let's assume that we have a database which stores passwords as md5 hashes. We can create another database that has md5 hashes of commonly used passwords. We can then compare the password hash we have against the stored hashes in the database. If a match is found, then we have the password.
- Guess– As the name suggests, this method involves guessing. Passwords such as qwerty, password, admin, etc. are commonly used or set as default passwords. If they have not been changed or if the user is careless when selecting passwords, then they can be easily compromised.
- Spidering– Most organizations use passwords that contain company information. This information can be found on company websites, social media such as facebook, twitter, etc. Spidering gathers information from these sources to come up with word lists. The word list is then used to perform dictionary and brute force attacks.
Spidering sample dictionary attack wordlist
Password cracking tool
These are software programs that are used to crack user passwords. We already looked at a similar tool in the above example on password strengths. The website www.md5this.com uses a rainbow table to crack passwords. We will now look at some of the commonly used tools
John the Ripper
John the Ripper uses the command prompt to crack passwords. This makes it suitable for advanced users who are comfortable working with commands. It uses to wordlist to crack passwords. The program is free, but the word list has to be bought. Download adobe creative suite 3. It has free alternative word lists that you can use. Visit the product website https://www.openwall.com/john/ for more information and how to use it.
Cain & Abel
Cain & Abel runs on windows. It is used to recover passwords for user accounts, recovery of Microsoft Access passwords; networking sniffing, etc. Unlike John the Ripper, Cain & Abel uses a graphic user interface. It is very common among newbies and script kiddies because of its simplicity of use. Visit the product website https://www.softpedia.com/get/Security/Decrypting-Decoding/Cain-and-Abel.shtml for more information and how to use it.
Ophcrack
Ophcrack is a cross-platform Windows password cracker that uses rainbow tables to crack passwords. It runs on Windows, Linux and Mac OS. It also has a module for brute force attacks among other features. Visit the product website https://ophcrack.sourceforge.io/ for more information and how to use it.
Password Cracking Counter Measures
- An organization can use the following methods to reduce the chances of the passwords been cracked
- Avoid short and easily predicable passwords
- Avoid using passwords with predictable patterns such as 11552266.
- Passwords stored in the database must always be encrypted. For md5 encryptions, its better to salt the password hashes before storing them. Salting involves adding some word to the provided password before creating the hash.
- Most registration systems have password strength indicators, organizations must adopt policies that favor high password strength numbers.
Hacking Activity: Hack Now!
How To Unlock Password Winrar
In this practical scenario, we are going to crack Windows account with a simple password. Windows uses NTLM hashes to encrypt passwords. We will use the NTLM cracker tool in Cain and Abel to do that.
Cain and Abel cracker can be used to crack passwords using;
- Dictionary attack
- Brute force
- Cryptanalysis
We will use the dictionary attack in this example. You will need to download the dictionary attack wordlist here 10k-Most-Common.zip
For this demonstration, we have created an account called Accounts with the password qwerty on Windows 7.
Step 1: Open a browser on your computer and head over to the crack zip rar online website.
Step 2: When the website has fully loaded in your browser, you need to input a valid email address. Then click 'Select file' to upload your encrypted RAR file.
Step 3: You need to tap on the 'Submit' button to start uploading your file.
Step 4: Once your file has been uploaded successfully, you will get a TaskID. Click 'Start recover' to trigger the process. If you want to check the process, you need to click the 'Click here to track it'.
Note
Even though you only need to pay for the result, I do not highly recommend this tool to you. It will take a very long time to unlock the encrypted RAR file with this online service. When tracked the recovery process of my RAR file, I found that the process started with 0.29%. Then it moved on to 0.39% and 0.49%. I still didn't get a result now.
Way 5: Official Way to Bypass WinRAR Extraction Password When You Know the Password
For some users, it is annoying to enter a password every time you want to open the RAR archive. If you know the correct password, it will be simple to bypass this password prompt. This can be accomplished with the help of WinRAR. Following is a detailed guide for you.
Step 1: Firstly, you need to download and install the WinRAR app on your computer. Then launch it.
Step 2: Open the password protected RAR archive with WinRAR app. When the file opens, click the 'Extract to' button to start extracting the RAR archive.
Step 3: Enter the correct password in the 'Enter password' dialog. Click 'OK' to continue.
Step 4: Then it will start to extract files from the RAR archive. You can then right-click on the extracted files and choose 'Add to archive' to create a completely new and unprotected RAR archive for your files.
Tip: How to Bypass RAR/WinRAR Password on Android
You may want to know how to bypass RAR/WinRAR password on Android phones. If you already know the correct password, you can download an application called ArchiDroid from Play Store to bypass the password protection. If you do not have any idea of the correct password, it may be hard to skip the RAR/WinRAR password. We have spent much time searching online, but we didn't find any application that can bypass RAR/WinRAR password on Android without knowing the correct password. Thus, the best solution for you is to choose an online service or transfer your password-protected RAR file to a Windows computer, then bypass the password with the above-mentioned methods.
What is Password Cracking?
Password cracking is the process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords. In other words, it's an art of obtaining the correct password that gives access to a system protected by an authentication method.
Password cracking employs a number of techniques to achieve its goals. The cracking process can involve either comparing stored passwords against word list or use algorithms to generate passwords that match
In this Tutorial, we will introduce you to the common password cracking techniques and the countermeasures you can implement to protect systems against such attacks.
Topics covered in this tutorial
What is password strength?
Password strength is the measure of a password's efficiency to resist password cracking attacks. The strength of a password is determined by;
- Length: the number of characters the password contains.
- Complexity: does it use a combination of letters, numbers, and symbol?
- Unpredictability: is it something that can be guessed easily by an attacker?
Let's now look at a practical example. We will use three passwords namely
1. password
2. password1
3. #password1$
Games People Play follows three women - a basketball wife trying to protect her family, a tenacious journalist trying to rebuild a tarnished career and a struggling actress looking to become a. BET has renewed 'Games People Play' starring Lauren London, Sarunas J. Jackson, Parker McKenna Posey, Karen Obilom and Jackie Long for a second season. From executive producers Tracey Edmonds, Angela Burt-Murray, Vanessa Middleton, and Kim Newton, the Games People Play TV show is a drama based on Burt-Murray's 2014 mystery novel. Games People Play (2019 TV series) From Wikipedia, the free encyclopedia Games People Play is an American drama television series, based on the novel Games Divas Play written by Angela Burt-Murray, that premiered on April 23, 2019, on BET. On November 13, 2019, the series was renewed for a.
For this example, we will use the password strength indicator of Cpanel when creating passwords. The images below show the password strengths of each of the above-listed passwords.
Note: the password used is password the strength is 1, and it's very weak.
Note: the password used is password1 the strength is 28, and it's still weak.
Winrar Password Remover
Note: The password used is #password1$ the strength is 60 and it's strong.
The higher the strength number, better the password.
Let's suppose that we have to store our above passwords using md5 encryption. We will use an online md5 hash generator to convert our passwords into md5 hashes.
The table below shows the password hashes| Password | MD5 Hash | Cpanel Strength Indicator |
|---|---|---|
| password | 5f4dcc3b5aa765d61d8327deb882cf99 | 1 |
| password1 | 7c6a180b36896a0a8c02787eeafb0e4c | 28 |
| #password1$ | 29e08fb7103c327d68327f23d8d9256c | 60 |
We will now use http://www.md5this.com/ to crack the above hashes. The images below show the password cracking results for the above passwords.
As you can see from the above results, we managed to crack the first and second passwords that had lower strength numbers. We didn't manage to crack the third password which was longer, complex and unpredictable. It had a higher strength number.
Password cracking techniques
There are a number of techniques that can be used to crack passwords. We will describe the most commonly used ones below;
- Dictionary attack– This method involves the use of a wordlist to compare against user passwords.
- Brute force attack– This method is similar to the dictionary attack. Brute force attacks use algorithms that combine alpha-numeric characters and symbols to come up with passwords for the attack. For example, a password of the value 'password' can also be tried as p@$$word using the brute force attack.
- Rainbow table attack– This method uses pre-computed hashes. Let's assume that we have a database which stores passwords as md5 hashes. We can create another database that has md5 hashes of commonly used passwords. We can then compare the password hash we have against the stored hashes in the database. If a match is found, then we have the password.
- Guess– As the name suggests, this method involves guessing. Passwords such as qwerty, password, admin, etc. are commonly used or set as default passwords. If they have not been changed or if the user is careless when selecting passwords, then they can be easily compromised.
- Spidering– Most organizations use passwords that contain company information. This information can be found on company websites, social media such as facebook, twitter, etc. Spidering gathers information from these sources to come up with word lists. The word list is then used to perform dictionary and brute force attacks.
Spidering sample dictionary attack wordlist
Password cracking tool
These are software programs that are used to crack user passwords. We already looked at a similar tool in the above example on password strengths. The website www.md5this.com uses a rainbow table to crack passwords. We will now look at some of the commonly used tools
John the Ripper
John the Ripper uses the command prompt to crack passwords. This makes it suitable for advanced users who are comfortable working with commands. It uses to wordlist to crack passwords. The program is free, but the word list has to be bought. Download adobe creative suite 3. It has free alternative word lists that you can use. Visit the product website https://www.openwall.com/john/ for more information and how to use it.
Cain & Abel
Cain & Abel runs on windows. It is used to recover passwords for user accounts, recovery of Microsoft Access passwords; networking sniffing, etc. Unlike John the Ripper, Cain & Abel uses a graphic user interface. It is very common among newbies and script kiddies because of its simplicity of use. Visit the product website https://www.softpedia.com/get/Security/Decrypting-Decoding/Cain-and-Abel.shtml for more information and how to use it.
Ophcrack
Ophcrack is a cross-platform Windows password cracker that uses rainbow tables to crack passwords. It runs on Windows, Linux and Mac OS. It also has a module for brute force attacks among other features. Visit the product website https://ophcrack.sourceforge.io/ for more information and how to use it.
Password Cracking Counter Measures
- An organization can use the following methods to reduce the chances of the passwords been cracked
- Avoid short and easily predicable passwords
- Avoid using passwords with predictable patterns such as 11552266.
- Passwords stored in the database must always be encrypted. For md5 encryptions, its better to salt the password hashes before storing them. Salting involves adding some word to the provided password before creating the hash.
- Most registration systems have password strength indicators, organizations must adopt policies that favor high password strength numbers.
Hacking Activity: Hack Now!
How To Unlock Password Winrar
In this practical scenario, we are going to crack Windows account with a simple password. Windows uses NTLM hashes to encrypt passwords. We will use the NTLM cracker tool in Cain and Abel to do that.
Cain and Abel cracker can be used to crack passwords using;
- Dictionary attack
- Brute force
- Cryptanalysis
We will use the dictionary attack in this example. You will need to download the dictionary attack wordlist here 10k-Most-Common.zip
For this demonstration, we have created an account called Accounts with the password qwerty on Windows 7.
Password cracking steps
- Open Cain and Abel, you will get the following main screen
- Make sure the cracker tab is selected as shown above
- Click on the Add button on the toolbar.
- The following dialog window will appear
- The local user accounts will be displayed as follows. Note the results shown will be of the user accounts on your local machine.
- Right click on the account you want to crack. For this tutorial, we will use Accounts as the user account.
- The following screen will appear
- Right click on the dictionary section and select Add to list menu as shown above
- Browse to the 10k most common.txt file that you just downloaded
- Click on start button
- If the user used a simple password like qwerty, then you should be able to get the following results.
- Note: the time taken to crack the password depends on the password strength, complexity and processing power of your machine.
- If the password is not cracked using a dictionary attack, you can try brute force or cryptanalysis attacks.
Summary
- Password cracking is the art of recovering stored or transmitted passwords.
- Password strength is determined by the length, complexity, and unpredictability of a password value.
- Common password techniques include dictionary attacks, brute force, rainbow tables, spidering and cracking.
- Password cracking tools simplify the process of cracking passwords.
